Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo

Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo
GitHub - elc0rr3Km1n0s/duckyempire: USB Rubber Ducky payload based on Empire Framework for Red Team engagements only
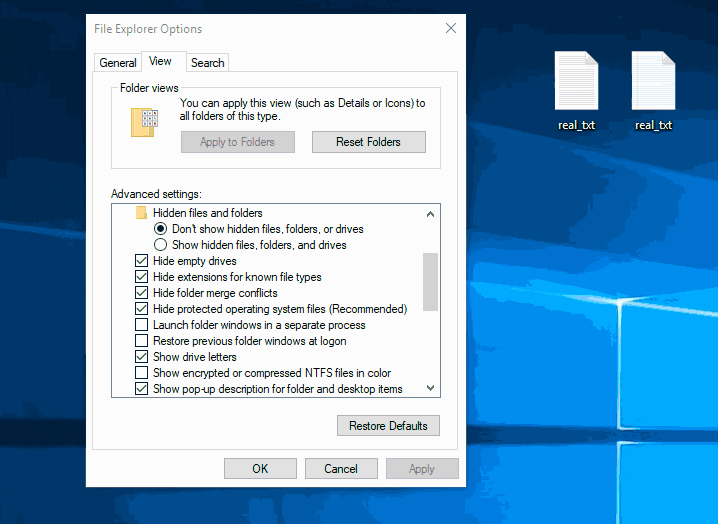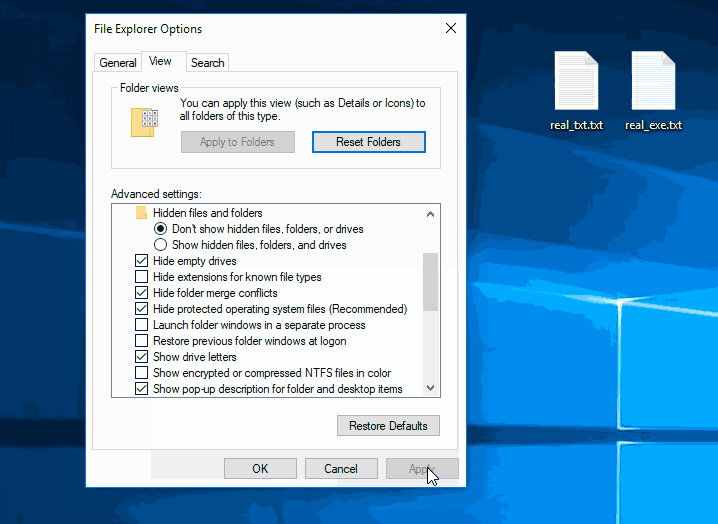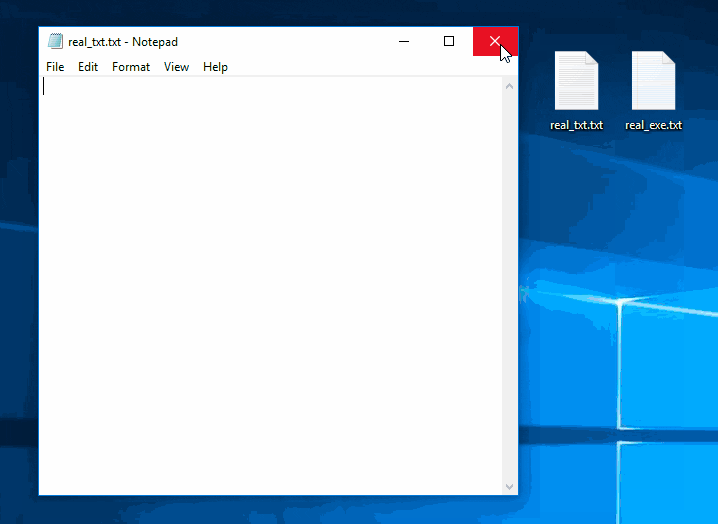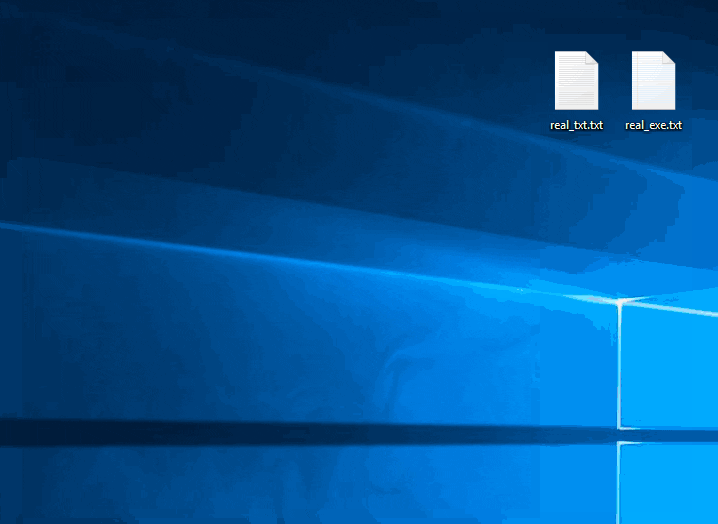
Hacking Windows 10: How to Create an Undetectable Payload, Part 1 (Bypassing Antivirus Software) « Null Byte :: WonderHowTo

Android for Hackers: How to Backdoor Windows 10 Using an Android Phone & USB Rubber Ducky « Null Byte :: WonderHowTo

TheFatRat Tutorial - Generate Undetectable Payload FUD, Bypass Anti-Virus, Gain Remote Access - HackingVision
















![PDF] Feasibility and Deployment of Bad USB | Semantic Scholar PDF] Feasibility and Deployment of Bad USB | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/88f8f64c045f210af9555d107f3b8aea507900bc/13-Figure3-1.png)
